CheckPoint, a security services firm, has released new information about a malware incorporated in certain applications installed outside of the Google Play Store. The CopyCat malware is capable of rooting the device, installing fraudulent applications, serving fraudulent advertisements, and stealing app installation credits.
All of these capabilities were made possible by the exploitation of certain security loopholes in the Android operating system, which should allow the malware to root the infected devices. The rooting of infected devices is in itself a major concern as it opens the user to a wide range of security concerns and exploits.
After the device is rooted, the malware then seeks to modify the code of the Android OS’s app launching system. The modification of the app launching system also allows the malware developers to monitor user activity. This information could then be used by the developers to earn ad revenue either by showing fraudulent advertisements on non-infected apps or by stealing app installation credit from other developers.
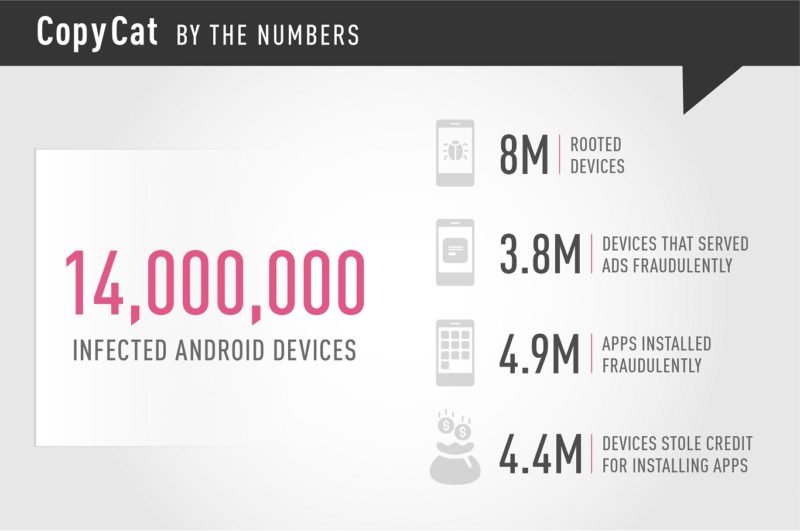
As developers may remotely change the attack objectives of a certain malware, it may also be used to infiltrate a corporate network or retrieve sensitive information stored within a device. The malware has infected around 14 million Android devices, more than half of which are found in Asia.
Out of the total number of infected devices, around 8 million have been rooted, likely without the knowledge of the user. In addition, fraudulent applications were installed by the malware in around 4.9 million devices while owners of 3.8 million devices have to deal with the advertisements served by the malware.